How does AES work?
AES processes blocks of 128 bits using a secret key of 128,192 or 256 bits. AES views a 16-byte plaintext as a two-dimensional array of bytes (s = s0,s1,s2......,s15). This transforms the bytes, columns and rows of the array to produce the ciphertext.
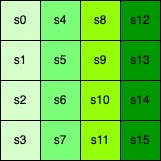
Note: s represents the state of AES and is viewed as a 4 X 4 array of 16 bytes
AES transforms its state by using SPN(Substitution and Permutation Network).
Four major building blocks of AES rounds are:
- AddRoundKey: XORs a round key to the internal state.
- SubBytes: Replaces each byte (s0,s1,s2,...,s15) with another byte according to an S-box.
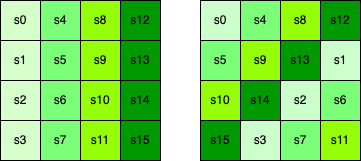
- ShiftRows: Shifts the i th row of i th positions for i ranging from 0 to 3.
- MixColumns: Applies the same linear transformation to each of the four columns of the state (i.e each group of cells with the same shade of green shown below).
AES will become insecure without:
- Key Expansion: Each round in the AES will be the same if the same key is used and are vulnerable to Slide Attacks.
- AddRoundKey: If encryption doesn't depend on the key, anyone could decrypt the ciphertext without a key.
- SubBytes: This adds strength cryptographic strength to cipher by introducing a non-linear operation. Without this operation, AES will just be a large system of linear equations which can be solved using simple algebra.
- ShiftRows: There won't be any change in a given column which never affect the other columns.
- MixColumns: States of other bytes won't be affected. A chosen plaintext attacker could then decrypt any ciphertext after sorting 16 lookup tables of 256bytes each.
How decryption works in AES?
Decryption in AES is followed by unwinding each operation by taking the inverse functions.
- Inverse lookup table of sub bytes reverses the SubBytes transformation.
- Inverse ShiftRows which shift row in opposite direction as the encryption.
- Inverse is applied on the MixColumns.
- AddRoundKey's XOR is unchanged because the inverse of an XOR is another XOR


