Modes Of Operation
- Electronic Codebook Mode (ECB)
- Cipher Block Chaining Mode (CBC)
- Counter Mode (CTR)
Electronic Codebook Mode - (ECB)
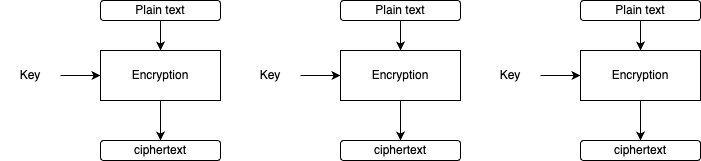
ECB is one of the most insecure and simplest modes of operation in BlockCipher. All blocks in plaintext (P1, P2...Pn) are processed independently by computing ciphertext. i.e C1 = E(K,P1), C2 = E(K,P2) and so on.
Encryption:
Decryption:
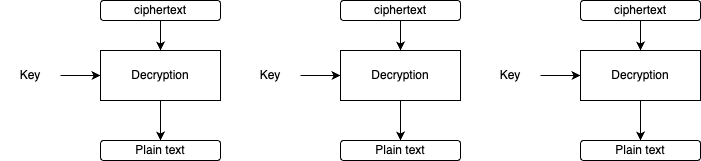
The major disadvantage of this mode is the lack of diffusion because an identical plaintext block is encrypted into identical ciphertext. Also, it doesn't hide the data patterns.
Cipher Block Chaining Mode - (CBC)
Cipher Block Chaining is a mode similar to ECB with a small change which constructs CBC to be more secure than ECB.CBC work by chaining the previous ciphertext block with the next ciphertext block. i.e In CBC instead of ith block Pi ,as Ci = E(K, Pi) it sets Ci = E(K, Pi (+) Ci-1).For encrypting the first block P1 there is no previous ciphertext block so, CBC takes a random initial value (IV). The initial value (IV) guarantees that two identical plaintexts will encrypt to distinctive cipher text.
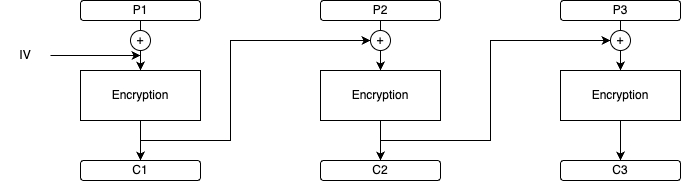
CBC mode makes each ciphertext dependent on all the previous blocks and ensures that identical plaintext blocks won't produce equivalent ciphertext blocks.
Decryption is faster in CBC mode than encryption because during encryption a new block Pi needs to wait for the previous block Ci-1. Every block can be decrypted in parallel simultaneously as long as the last ciphertext block is known.
Counter Mode - (CTR)
CTR mode is hardly a block cipher mode. CTR mode turns a block cipher into a stream cipher that simply takes bits and returns the bits. This block cipher won't convert plaintext data rather it transforms the blocks composed of a counter and a nonce. The counter is an integer that is incremented for each block. No two blocks should use the same counter within a message.
Nonce should only be used once. It will be the same for all the blocks in a single message. The same nonce should not be utilised for two different messages.
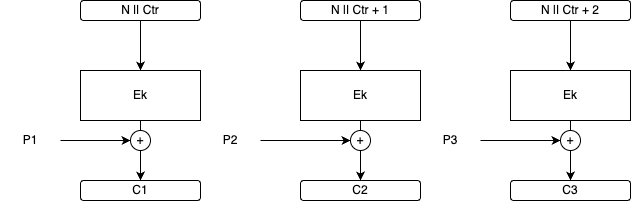
A nonce is supplied by the encrypter and sent with cipher text to the decrypted. A nonce need not be random but it should be unique because the one-time-pad shouldn't be reused.
CTR mode is faster than any other mode. Not only it is parallelizable but also one can start encrypting before knowing the message by picking nonce and XORing the stream with the plaintext.


